With data protection regulations holding more weight than in the past, it becomes important for individuals and corporations to protect data and network security. One way to do that is by having in place intrusion detection system to monitor and send alerts when there is suspicious activity.
In this article, we will be covering what intrusion detection systems are, how they work and their benefits. Read below:
What Is an Intrusion Detection System?
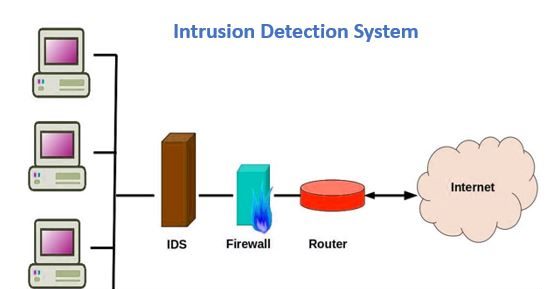
An Intrusion Detection System (IDS) is a software or device that monitors network traffic for malicious or suspicious activity as well as policy violations. Once these activities are discovered, the IDS sends out alerts to inform management or a technician of the event and/or responds to the detected intrusion.
Types of Intrusion Detection Systems
Intrusion detection systems exist in varied forms from tiered monitoring systems to antivirus software. However, there are two categories that capture the nature and methodology of IDS:
- Network Intrusion Detection System (NIDS): both inbound and outbound network traffic are monitored for anomalies.
- Host-based Intrusion Detection System (HIDS): all operating system files of computers such as Chromebooks and devices with direct access to a network are monitored.
However, under the types of intrusion detection systems, there are two-subsets. Both NIDS and HIDS can either be signature-based intrusion detection systems or anomaly-based intrusion detection systems.
- Signature-based Intrusion Detection System (SIDS): the SIDS monitors either networks or operating system files of devices for known patterns of malicious instructions from malware. These patterns are compared against a database of attack signatures. Antivirus software is examples of SIDS.
- Anomaly-based intrusion detection system (AIDS): unlike SIDS, AIDS are designed to monitor for unknown attacks or patterns. Machine learning technology is leveraged to enable the system to detect and adapt to attacks based on a broad model and not just signatures.
How Can Intrusion Detection Systems Be Utilised?
The average IDS can be put to use under the following scenarios:
- As a monitor for the operation of files, servers, routers and firewalls needed by other security controls to detect, prevent or recover from cyberattacks.
- As an avenue for administrators to organize and understand relevant operating system audit trails or logs that are difficult to track.
- To provide an alternative for non-tech staff to partake in managing system security.
- As an attack signature database for all instructions to be matched.
- As an alert system for reporting IDS activities or security breaches.
- To act as an attack blocking system.
Benefits of Intrusion Detection Systems
With the various capabilities of an intrusion detection system, it is safe to say that they provide organizations with several benefits. Some of the key ones include:
-
Identifying Security Incidents
With the IDS any individual or organization can identify security incidents and analyze them based on their type and quantity. This information also helps organisations in strengthening their security system also implementing effective mitigants and controls against these attacks.
Also, bugs or problems that affect network devices and their core processors can be identified. The metrics of these identified attacks can be further analyzed to predict future incidents.
-
Monitor Regulatory Compliance
Remember how we said earlier that data protection regulations are very important in the present-day clime? Well, it is not only data protection regulations but every other regulation that deals with ensuring security and confidentiality of networks and data. These regulations are important not only because of the fines and penalties that arise from non-compliance but also the damage they can cause to the reputation of an institution.
With an IDS, the modern-day organization gains greater visibility of the strength of its networks and systems and ensures they meet regulatory standards. Also, an organization can use the logs from the IDS as documentary evidence of compliance.
-
Identify System Gaps
With the IDS, organisations are better able to respond to security risks. Where the organisation’s system lacks, the IDS will identify gaps which the organization shall improve upon. The IDS can also be used as sensors to detect hosts and devices on a network, inspect information within these network packets and identify the operating systems of the service in use. In summary, the IDS is an efficient means of data collection to improve security systems.
Is There a Difference Between an IDS and an IPS?
IPS stands for Intrusion Prevention System. An IPS are similar to an IDS in the sense that they can be used to monitor, log and report suspicious activities, they also go a step further by blocking those potential threats without the intervention of a system administrator. On the other hand, IDS need the involvement of a system administrator before stopping any detected threats. So, the major difference lies in the configuration.
Which Is Better: Host-based or Network Intrusion Detection Systems?
Although both intrusion detection systems have their pros and cons, the host-based intrusion detection system covers a wider spectrum than the network intrusion detection system. With a host-based intrusion detection system, threats on network traffic and within the operating files are monitored.
Conclusion
As more advancements and innovations are made in technology, being able to protect the network and data security is important. Intrusion detection systems are one such example of tools that can help with that.